Wireless Tech Field 2 – Recap and first looks
January 28, 2012 8 Comments
This past week, I attended the Gestalt IT Wireless Tech Field 2 event hosted by several leaders of the wireless industry in San Jose, CA. The Tech Field day events are an opportunity for vendors and manufacturers to get in front of a highly focused group of delegates to tell their own story, on their own playing field. The Wireless specific event is the brainchild of Steven Foskett and Jennifer Huber and I consider myself privileged to have been able to participate in this very prestigious event – now for the second time! This event was sponsored by industry leaders in the wireless space – Aerohive, Meraki, MetaGeek, Ekahau, Aruba, HP, and Ruckus (in order of visit). The delegates for the event were given the opportunity to meet with these companies, in many instances at their home offices, to share first hand their stories and visions for what they feel is the market drivers in the wireless space as well as their respective visions for what the future of wireless is going to bring. This post will be the first of several as I dive into each of our sessions with many of the vendors and share my take on the vendors, their products, and how I perceive them to fit ‘in the industry’.
This Wireless Tech Field day was preceded by the first wireless symposium where members of the industry and media were invited to participate in an open discussion on the future of wireless with a focus in particular on upcoming technologies 802.11ac/ad (gigabit WiFi), 802.11u (Hotspot 2.0), and Bring Your Own Device (BYOD) technologies. Devin Akin (Aerohive), Carlos Gomez (Aruba), Paul Congdon (HP Labs), and GT Hill (Ruckus) treated us to their vision of how these topics will shape and form the foreseeable future in the wireless industry. I’ll also be exploring these various topics in upcoming blog posts, so consider that a teaser! 🙂
Each of the sponsors of the WFD event each brought something special or different to the table. I think one of the most important things I learned during the event is that, when given the opportunity, each manufacturer tells a compelling story when given the opportunity to. I consider myself a fairly impartial technologist so it was refreshing to be able to receive these messages in their native, or ‘best case’ format highlighting the various strengths that each company has to offer:
Aerohive continues on their self-proclaimed mission to rid the world of controllers. Aerohive is rolling along with their ‘protocols are free’ mantra to bring solutions rapidly to market in a low-cost, easy to deploy fashion. Their cooperative control architecture enables many of the features of a centralized controller based solution and they are extending this into the routing world with the introduction of the BR-100 branch edge router. This device is managed ‘by the cloud’ – by either using the Hive Manager Online solution that is hosted by Aerohive or hosting your own ‘private cloud’ instance of the rapidly evolving NMS.
Meraki, to be perfectly frank, was perceived by many of the delegates as the ‘underdog’ of the event and many of us had some pretty negative preconceptions of who they were and what they do. I think it’s safe to say that Meraki portrayed a strong showing overall and rapidly showed the room at large that they’re clearly more than a niche player in the wireless space. They showed off their NMS platform and gave us some ‘under the hood’ insights into their operations overall. The way Meraki is able to manage and aggregate data from the vast (that word seems woefully insufficient) deployment of edge Access Points was staggering.
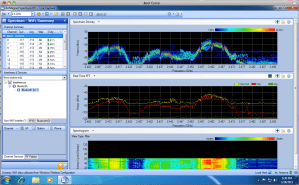
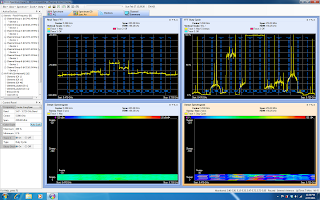
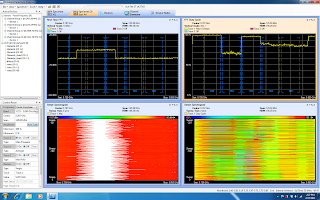
MetaGeek once again showed off to the TFD delegates. Last year at the first TFD event, they stole the show by showing off their low cost – feature rich PC based spectrum analyzer product. This year, demonstrating the agility that is impossible in a larger organization, they showed off their extension of ‘wireless visualization’ products – Eye P.A. This play on a TLA stems from their ‘eyeball’ view of Packet Analysis. As an organization that is clearly focused on getting information to a place that its easy to understand, they presented (showed off?) a pre-release version of this product. It’s safe to say that all of the delegates were blown away by the unique and innovative show of application development. MetaGeek has sprung up from seemingly nowhere to make a name for themselves in a technology that is exciting and that knows no growth boundaries.
Ekahau came to the table with their site survey product ESS (Ekahau Site Survey), the mobile version of their vision for tablet-based site surveys, and their tags. As an avid user of competing site survey products, I can clearly see that I’ll be rethinking my overall approach to performing the most important part of a wireless deployment – the site survey. I look forward to some hands on time with their android tablet compatible piece of this software. This is clearly a place that the major competitors are deficient in and Ekahau stands to be the first to market with an exciting product. Almost running out of time at the event, we got a very quick overview of their RTLS tag for wifi based deployments. As a side note to the Ekahau team directly, you have enough exciting things to talk about that maybe next time two sessions would be appropriate. 🙂
Aruba brought out the big guns during their sessions showing off their Aruba Instant product – essentially a wireless controller running on an AP. Those of you familiar with the now all-but-defunct WDS can consider this WDS in a fully automated, steroid enhanced feature set enabling rapid deployments of premise-based and managed lightweight deployments. After a good discussion regarding Spectrum Analysis, we dove off into the BYOD deep end with a realtime display of managing guest devices including a strong iOS MDM application utilizing products from their recent Amigopod acquisition.
HP gave the delegates a good overview of their 3×3:3 wireless Access Points including their newly launched outdoor product the MSM-466R. They also showed off their newest member of their controller line the MSM720 including some fervently discussed licensing features such as a discreet ‘advanced feature set’ as well as the ability to pool AP licenses across controllers.
Ruckus closed out the event with us by bringing a deep dive discussion regarding their approach to RF management. Ruckus gets top marks for their no holds barred approach to interacting with the delegates. Future sponsors of the event can take a page from their book – using a combination of geek + relevance to the table. Hands down, Ruckus had the room enthralled by the discussions and philosophies surround their approach to the market – no small feat for the last sponsor of the event.
Needless to say, the WFD event was exciting, exhausting, fun, and educational for everyone involved. As a delegate, I received a variety of products and marketing swag from the vendors with the understanding that I’m under no obligation to do anything with it that I don’t want to. The opinions that I intend to express from evaluating and trying out these products are my own and I’m also under no obligation to be positive or sway my opinion based on any gifts, equipment, or swag I have received. I look forward to digging deeper into these manufacturers and sharing what I feel and offering my honest, direct opinions on them. I hope you’ll stay tuned for future posts where I discuss the event, sponsors and products!